Understanding VPNs vs DNS Encryption: What Actually Protects Your Privacy?
There's a lot of noise out there about online privacy tools. VPN companies spend millions on ads telling you that you need their service to be safe online, while other articles claim that encrypted DNS and HTTPS have made VPNs obsolete. The reality, as usual, is more nuanced than either side wants to admit.
I recently helped someone work through exactly this question, and it made me realize how much confusion exists around what these different tools actually do. So let's break down what VPNs and DNS encryption really protect, and when you might need each one.
The two-step dance of web browsing
Before we can talk about privacy tools, we need to understand what actually happens when you visit a website. It's not as simple as it might seem.
When you type https://example.com into your browser, two separate things need to happen:
- DNS lookup: Your device asks "where is example.com?" and gets back an IP address like
93.184.216.34 - HTTP request: Your device connects to that IP address and asks for the webpage
These are completely separate network requests, and they can be encrypted independently. This is really important to understand because different privacy tools protect different parts of this process.
Without any protection, both of these requests happen in plain text. Your ISP, coffee shop WiFi operator, or anyone else along the network path can see exactly which websites you're looking up and connecting to. They can't see the content of HTTPS websites (thanks to TLS encryption), but they know you visited them.
DNS encryption: Hiding your lookups
DNS over TLS (DoT) and DNS over HTTPS (DoH) solve the first part of the privacy puzzle. Instead of sending DNS queries in plain text, they encrypt the "where is example.com?" conversation.
DoT wraps your DNS queries in TLS encryption, the same technology that protects HTTPS websites. It's effective, but it's also obvious - anyone monitoring your traffic can see that you're making encrypted DNS requests, even if they can't see what you're asking for.
DoH is sneakier. It disguises DNS queries as regular HTTPS traffic, making them much harder to detect and block. From a network observer's perspective, it just looks like you're browsing the web normally.
Both approaches mean you're trusting a DNS provider like Quad9, Cloudflare, or NextDNS instead of your ISP's DNS servers. The DNS provider will see all your lookups, but your ISP won't.
Here's what changes: if you're using DoH with Quad9, your ISP can no longer see that you looked up "social-media-site.com" or "news-site.com". But they can still see that you subsequently connected to the IP addresses for those sites.
VPNs: The traffic proxy approach
VPNs work differently. Despite the name "Virtual Private Network," what services like Mullvad, ProtonVPN, or Nord are really doing is proxying all your traffic through their servers. It's less about creating a private network and more about changing where your traffic appears to come from.
When you connect to a VPN, all your internet traffic gets wrapped up in an encrypted tunnel to the VPN provider's servers. From there, it goes out to the wider internet as if it's coming from the VPN server, not from you.
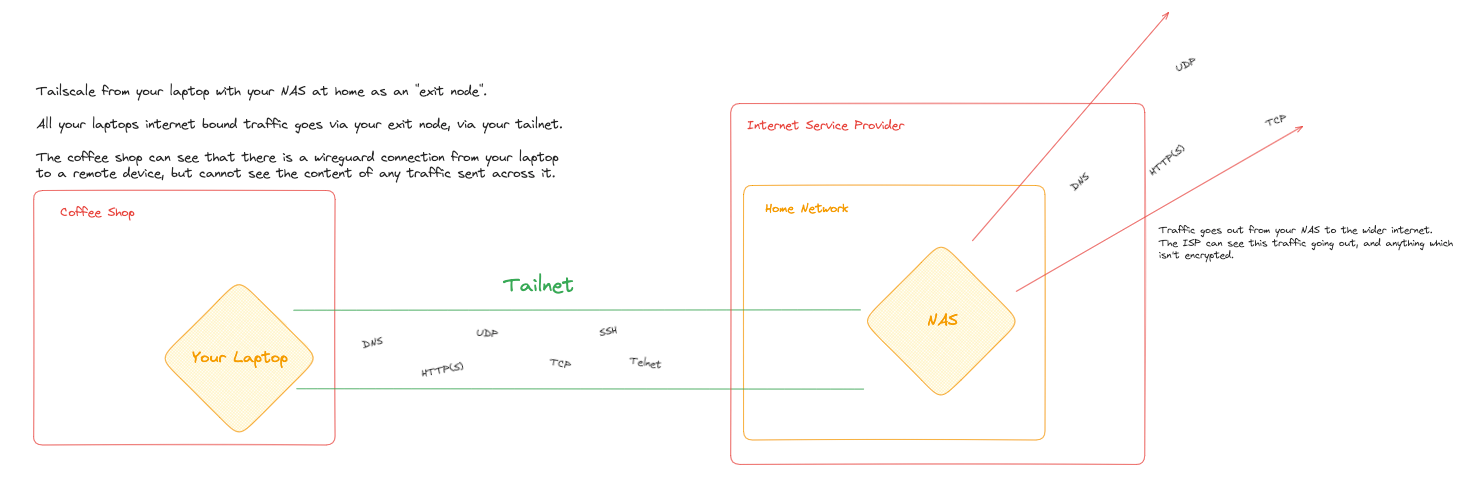
You can also create your own version of this with something like Tailscale exit nodes, where you route your traffic through a server you control (maybe an AWS instance or a home server) rather than through a commercial VPN provider's infrastructure.
The key difference is where you're placing your trust. With a commercial VPN, you're trusting the VPN company instead of your ISP. With a self-hosted exit node, you're trusting your cloud provider or home internet connection instead of whatever network you're currently on.
Either way, you're not eliminating trust - you're just moving it somewhere else.
Take care when selecting which VPN you wish to trust, many of the cheaper ones are selling data to advertisers.
Three scenarios compared
Let me walk through three different setups to show how these tools work in practice. I'll use the example of browsing the web from a coffee shop, since that's a common scenario where people think about privacy.
Scenario 1: No protection
You're at a coffee shop, connected to their WiFi, browsing normally with no privacy tools enabled.
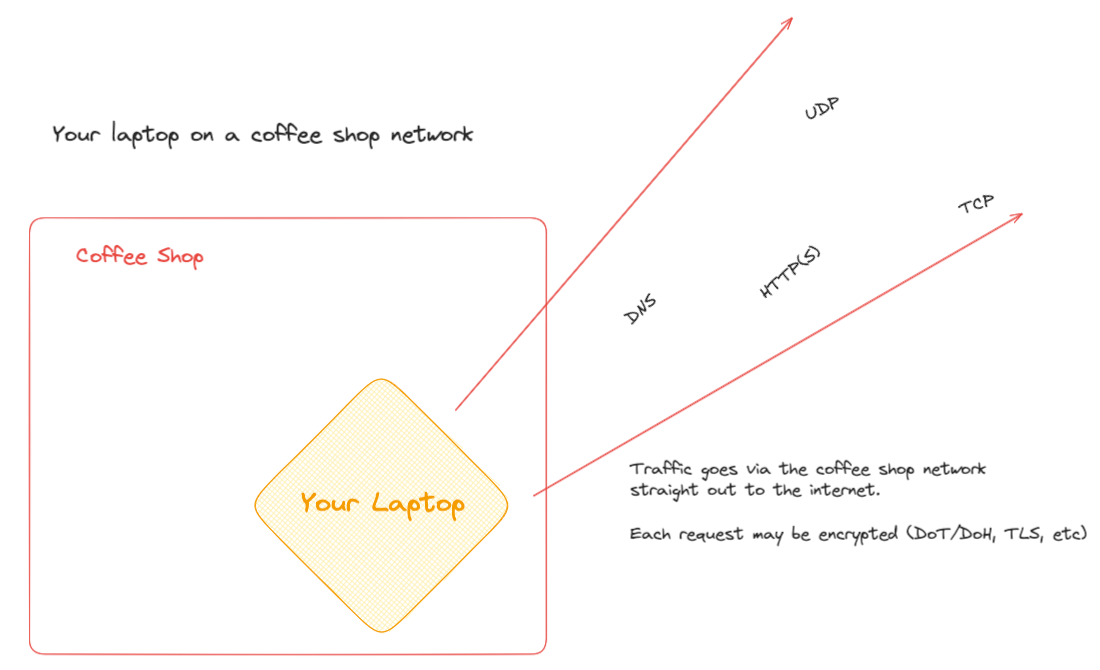
The coffee shop can see every DNS lookup you make and every IP address you connect to. They can't see the content of HTTPS sites, but they know you visited them. Your ISP back home doesn't see any of this traffic because you're not using their network.
Scenario 2: DNS encryption + HTTPS everywhere
Now you've configured your device to use DoH with Quad9, and you're making sure all websites use HTTPS.
The coffee shop can no longer see your DNS queries - those are encrypted and going directly to Quad9. But they can still see you connecting to IP addresses afterward. So they might not know you looked up "private-forum.com," but they can see you connecting to whatever server hosts that site.
Your traffic is more private, but not completely hidden from the local network.
Scenario 3: VPN + DNS encryption + HTTPS
Finally, you're routing everything through a VPN like Mullvad, still using encrypted DNS, still ensuring HTTPS everywhere.
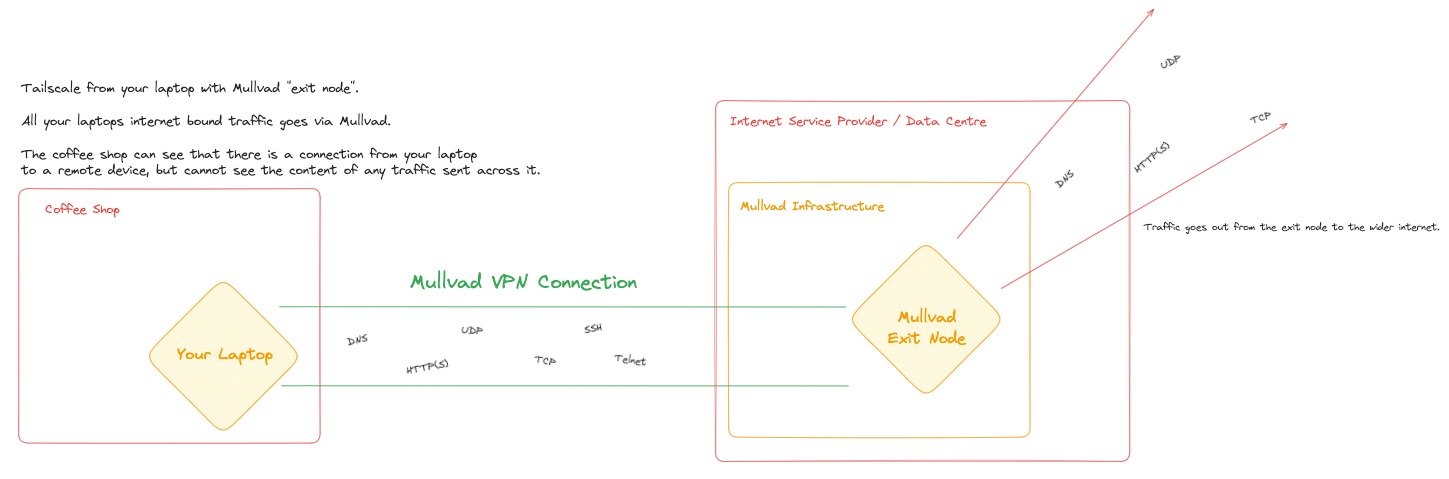
Now the coffee shop can only see encrypted traffic flowing between your laptop and Mullvad's servers. They have no idea what websites you're visiting or what you're doing online. All your DNS queries and web requests are happening from Mullvad's network, not the coffee shop's.
The trade-off is that Mullvad can now see your traffic patterns (though not the content of HTTPS sites). You've shifted trust from the coffee shop and your ISP to Mullvad and whatever network infrastructure they use.
Choosing your approach
So which approach should you use? It depends entirely on what you're trying to protect against.
If you're mostly concerned about your ISP building a profile to sell to advertisers, DNS encryption plus HTTPS might be perfectly adequate. Your ISP won't know what sites you're looking up, and they can't read the content of your web browsing.
If you're on untrusted networks regularly (airports, hotels, coffee shops), a VPN adds a valuable layer by hiding your browsing patterns from the local network operator. It's not that you don't trust them exactly, it's that you don't know who they are or what they're doing with the data.
If you're dealing with more serious threats - maybe you're a journalist in a country with an oppressive government - you'll want to think carefully about which VPN provider to trust, or consider more sophisticated tools like Tor.
The key is being honest about your threat model. I work in the UK and occasionally use coffee shop WiFi. For me, DNS encryption handles most of my concerns, and I'll flip on a VPN if I'm somewhere I don't trust the local network. Someone in a different situation might need a completely different approach.
My personal setup
In my day-to-day life, I use DoH with a DNS provider I pay for, and I have my browser configured to ensure everything uses HTTPS (which is the default these days anyway). I'll use a consumer VPN if I need to appear to be in a different location, or if I don't trust the network I'm on more than I trust the VPN provider.
This works for my threat model, but it might not work for yours. The important thing is understanding what each tool actually does, so you can make an informed decision rather than just following marketing advice.
The bottom line
Here's what I wish more people understood: there's no perfect privacy solution. You're always trusting someone, because your traffic has to exit onto the internet somewhere. The question is who you want to trust, and what you're trying to protect against.
DNS encryption is great for hiding your browsing patterns from your ISP. VPNs are great for hiding your activity from local networks and changing your apparent location. Using both together gives you more privacy than either alone, but it also means trusting more parties with your data.
The most important thing is to ignore the marketing noise and understand what these tools actually do. Once you know that, you can make decisions that actually make sense for your situation.
Don't let VPN companies scare you into thinking you need enterprise-grade protection to check email at Starbucks. But also don't let the "HTTPS solved everything" crowd convince you that network-level privacy doesn't matter if you're facing real threats.
As with most things in technology, the answer is "it depends" - and now you have the knowledge to figure out what it depends on for you.
Member discussion